SERVICES
Secure IoT Ecosystem
IoT is forcing many business leaders to reassess their decentralized approaches to cyber risk management
Securing IoT Devices and Data
Internet of Things offers new ways for businesses to create value, at the same time constant connectivity and data sharing also creates new opportunities for information to be compromised.
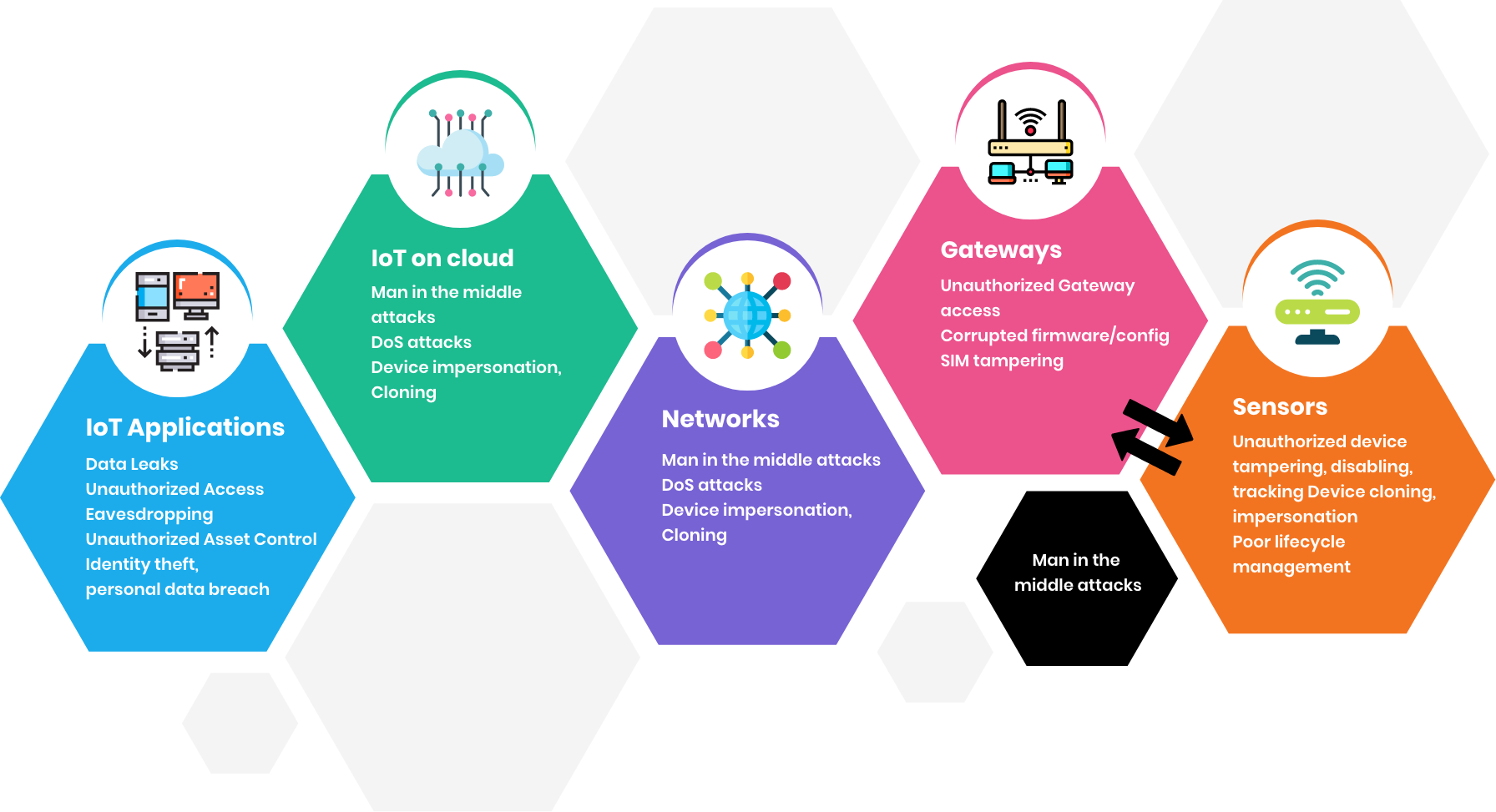
With IoT, sensors collect, communicate, analyze, and act on information, offering new ways for technology, media and telecommunications businesses to create value—whether that’s creating entirely new businesses and revenue streams or delivering a more efficient experience for consumers. In parallel, this also opens up new threats where all that information can be compromised, and devices can be commanded to operate erratically, and even dangerously in certain cases. Not only is more data being shared through IoT, among many more participants, but more sensitive data is being shared. As a result, the risks are exponentially greater.
IoT is an inherently shared ecosystem and operating model that crosses public and private sectors. Yet today, there are no uniform standards governing the IoT. Threats to business can manifest at the physical or device layer, in networks or in the different applications used to consume IoT data or to send commands/control instructions to devices and connected equipment. Based on the specific IoT architecture being planned for customer needs, the threats need to be identified early on and the appropriate protective measures and solutions need to be put in place both during design and build phase and post deployment.
How Tabono Can help you
At Tabono our experts look beyond network and application analytics using various technologies to make necessary adjustments with the system. We look for multiple solutions to resolve data breach using state-of-the-art tools by hiring the best experts in the field. This gives our customers an opportunity to boost productivity, set parameters based on real-time granularity at each network, and to remediate cyberattacks. Our AI team utilizes new machine learning methods to find loopholes in the devices, they are still the most effective weapon to analyze data in real time, correlate information, distinguish patterns, and make precise forecasts based on the data gathered.