SERVICES
Risk Advisory and Compliance Management
Manage risk and compliance of your ecosystem and security at the same pace
Third Party Risk Management
Having a vendor risk management in place helps you to manage and monitor risks resulting from engaging third-party vendors including suppliers of information technology (IT) products and services.
Tabono’s risk management consultants can help you analyze and protect from operational, regulatory, financial and reputational risk raising out of engagement with vendors. As you increase your outsourcing pie, vendor and third-party risks increase and become an integral part of your enterprise risk management framework.
Tabono’s TPRM framework is a comprehensive tool to help you chart your relationship with the vendor from due diligence and helps prevent legal and compliance breaches, loss of personally identifiable information (PII), information and data security risks and loss of intellectual property.
We help create a vendor risk management plan that will identify and outline behaviors, access and service levels of the vendor.
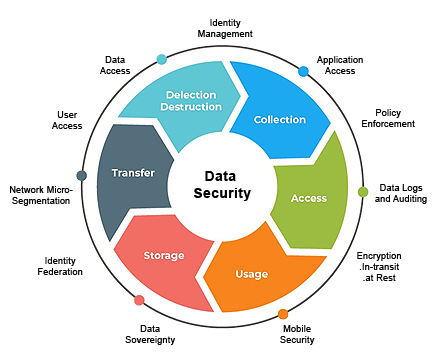
Data Security
Data security refers to a set of standards protecting data from unauthorized access and corruption throughout its lifecycle. Data security includes data encryption, hashing, tokenization and key management practices that protect data across all applications and platforms
The primary aim of data security is to protect the data that an organization collects, stores, creates, receives or transmits. Compliance is also a major consideration. It doesn’t matter which device, technology or process is used to manage, store or collect data, it must be protected. Data breaches can result in litigations and huge financial losses. The importance of shielding data from security threats is more important today than it has ever been.
Tabono Data Security Framework (DSF)is a tool-based approach to managing the flow of an information system’s data throughout its life cycle: from creation and initial storage to data disposal, when the data gets obsolete.
Tabono consultants can help you manage the complete data life cycle from data collection to data purging. The process of encryption, masking and resilience is managed by our consultants and can guide you to safely collect data from mobile endpoints, your IOT devices and work with you. Data maintenance is a precursor to the value generation phase and includes data cleansing, enrichment and the most ubiquitous ETL flow.
Tabono consultants can help you to safely analyze data and ensure data governance challenges are met all the way through data usage, archival and data purging as per the industry standards and norms. Whether you need to comply with GDPR regulations or PHI/HIPAA legislation, DSF has the built-in expertise to prepare and protect your business where it counts.
PCI Compliance
The Payment Card Industry Data Security Standard (PCI DSS) applies to companies of any size that accept credit card payments. Tabono can help your company accept card payment, and store, process and transmit cardholder data, and help host your data securely.
Tabono PCI Compliance team can help you to protect stored cardholder and customer data by guiding you to plan, manage or avoid storage of sensitive data through our Data Security Framework (DSF).
We can also guide you to properly encrypt and protect any data during transmission. We can also establish strong access control measures by restricting access with authentication, authorization and encryption practices in your environment to protect cardholder data.
GDPR Compliance
The General Data Protection Regulation (GDPR) is a regulation in EU law on data protection and privacy in the European Union (EU) and the European Economic Area (EEA). if you store data relating to citizens in the European Union (EU) you will need to comply with the latest GDPR regulations. As controller and processor of personal data you are required to put in place appropriate technical and organization measures to implement data protection principles.
Tabono’s consultants can help design information systems with privacy in mind, with highest-possible privacy settings by default.
Tabono Data Security Framework (DSF) can help prepare a roadmap by analyzing your company’s data footprint in the EU, control gap assessment, control visibility and access of data and developing a breach response plan to meet GDPR notification requirements.
NIST Compliance
National Institute of Standards & Technology (NIST) is an agency within the US Department of Commerce. NIST also manages standards and guidelines to help federal agencies meet the requirements of FISMA (Federal Information Security Management Act).
Tabono’s NIST compliance services, gap assessment, policy and process development implementation support and maintenance & management.

ISO27001 Compliance

Tabono can help you in your compliance and certification journey for the world’s most widely accepted security standard ISO 27001:2013. Equipped with certifications like ISO27001 and being a lead auditor and implementer coupled with decades of experience in implementing Information Security Management System for global corporations, our consultants can speed up your journey to compliance and help you improve the security posture of your organization.
SOC2 Compliance
If you are providing services to global organizations and particularly to clients in the United States, you may be required to demonstrate compliance to American Institute of CPAs developed Service organization Controls.
SOC2 compliance provides confidence to your customers on your processes and security posture. Our consultants with expertise in designing and implementing SSAE18 compliant controls can help build processes and controls to get certified in SOC2 Type 1 and Type 2.

CSA Star Compliance

CSA star is the gold standard for cloud security. If you provide cloud-based solutions and services to clients, CSA Star certification can give reasonable confidence in your security posture and can give you edge against your competitors. Alathea team equipped with certifications like CCSP & CCSK and with extensive expertise in assessing and implementing security controls compliant to CSA star requirements can help you in your journey to CSA star certification.